Phish Philtering
Deceptive techniques used by phish sites
As I’ve seen a lot of articles on LinkedIn recently about the use of glyphs (characters) misused to look like other characters so as to disguise a malicious URL as a legitimate URL, which reminded me of this article on such homoglyph attacks. It originally appeared on Kevin Townsend’s ITsecurity UK site, to which I was a frequent contributor, along with several other independent researchers. Sadly, a flurry of cyberattacks put that site out of business, but I have Kevin’s permission to reuse articles that were originally posted there. This article isn’t only about homoglyph attacks, but illustrates some other ways in which a phishing site might be disguised in order to attract victims. Among the links it includes is a harmless site that was, nonetheless, set up specifically as an example of a site that was not what it appears to be from a given URL. (A technique I’ve actually used a couple of times in the past, but in this case it’s an ESET site.)
I recently posted an article on the ESET blog about recognizing phishing messages. It covers quite a lot of ground that I don’t intend to go over again here, though I’ll include a quick summary at the end of this article, to give you an idea as to whether it’s worth reading – or recommending to others. Well, you never know. However, for some people the ways that a URL might be camouflaged as something resembling a legitimate site name so as to trick a victim into clicking on a malicious site has proved to be even more of a draw than the horrible visual (and non-visual) puns I included.
Happily, many of the tricks for obscuring URLs that were commonly used when I first starting researching phishing techniques have been addressed in common browsers, so that some techniques as described in older articles will no longer work as expected. Don’t take that for granted, though: one of those tricks is to put a legitimate looking site-name at the beginning of the URL, on the assumption that the browser will ignore anything between the initial ‘http://’ and an ‘@’ character. Here’s an example: https://lloyds-bank@www.welivesecurity.com/2013/05/29/phishing-the-click-of-death/. In a quick and quite unscientific test, I was surprised to find that this URL took me quite happily to www.welivesecurity.com/2013/05/29/phishing-the-click-of-death/ in Chrome, though Internet Explorer told me that it couldn’t find the site. [When I tried this much more recently (2025) in Chrome I was still taken to the WeLiveSecurity page, but the real URL was shown in at the top of the page without the ‘Lloyds Bank’ URL that precedes the @ symbol – your browser’s mileage may vary.]
All the more reason for passing the cursor over the URL to see if the apparent URL and the one the browser actually sees are a match. Sadly (if you’ll allow me to quote myself…):
…many large organizations, including the big banks, use multiple domains for various purposes, and some outsource mail and other services to external companies whose domains don’t appear to have anything to do with the provider. Unfortunately, this is one of the practices that make the scammer’s life easier, but it’s a practice too firmly ingrained in modern business to expect it to be discontinued any time soon.
Here’s a very simple example of a link that looks quite different to the site it really links to: nice-site.co.uk. Yes, it really goes to that WeLiveSecurity site again. Other tricks include using one or more redirects (very commonly used in malware dissemination) and the use of shortened URLs.
Using a domain that looks like a known real address but is slightly and inconspicuously different is standard practice for phishers, and not always easy to detect. A simplistic example might be something like IIoydsbank.com or barcIays.com, where I’ve substituted a capital ‘I’ for each lowercase ‘L’.
We see a common variation of this approach known as a homoglyph attack: in the Unicode character set there are many exotic characters that look to the casual eye (at least in some fonts) very much like ASCII characters, but are for purposes of identifying a web address completely different.
In the original blog, I just cited some examples:
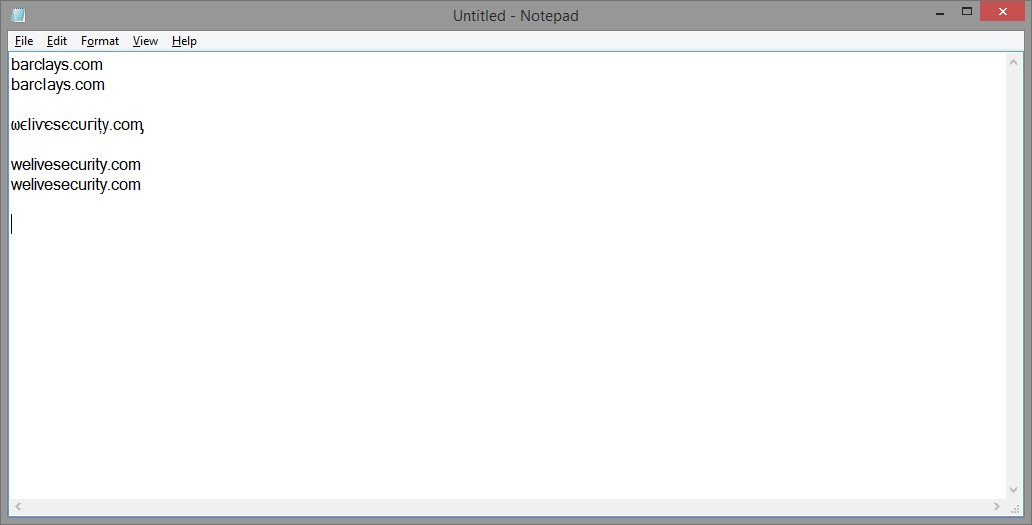
In the following representation of the ESET blog domain ‘welivesecurity.com’, ωϵІіѵєѕєсᴜᴦіțу.ϲοᶆ not one character is actually the US-ASCII character it resembles. Sitting here surrounded by standard Latin characters, the word looks quite odd (especially as the CMS doesn’t allow me much flexibility with the font size or character set), but what if it was just one character different with a carefully chosen font and font size? For example, welivesecurity.cοm. (In this case, that ‘o’ is actually an omicron.)
Subsequently, my friend and former colleague at ESET, Bruce Burrell, suggested that if readers were to paste those two bogus welivesecurity.com URLs into Notepad (Other Text Editors Are Available), then search for the letter ‘o’ it would be a good ‘live’ demonstration of the principle of this kind of attack, and I modified the article accordingly.
Here, though, I simply used a screenshot to illustrate the principle.
In the first pair (barclays.com), the ‘L’ in one is actually an uppercase ‘I’. There is a visible difference (if the image is large enough) between the two because I used a proportional font (Microsoft Sans Serif). The absence of serif (the twiddly bits at the top and the bottom of the ‘I’ accentuates the similarity between the two characters (just a straight vertical line in each case), the kerning is slightly different in each case, so one of the pair is slightly wider than the other. But can you tell which one is bogus? If you can, you’re probably a typographer…
The version of welivesecurity.com that consists entirely of homoglyphs is pretty easy to spot, though it might be more convincing in a different typographical context.
However, one of the second pair of addresses really does say welivesecurity.com, while the other includes an omicron instead of an ‘o’. And I can’t tell which is which by eye: maybe you can do better. (Give up? The fake is the first one…)
Here’s a summary of indicators of possible malice in a potential phishing message. Of course there’s more detail in the original article.
1) Does the message really show that the sender knows anything about you, let alone that you already do business with him?
2) Expect the worst from attached files and embedded links.
3) Take elementary precautions (like passing the mouse cursor over the link)
4) Don’t let threats get to you and be panicked into clicking incautiously
5) Don’t be click-happy and rely on security software to detect everything
6) Don’t fall for slick presentation: phishers are much more sophisticated nowadays.
7) Unless you’re a security expert, consider checking out some of the resources listed in the article for more information.
Of course, there’s plenty of information published by other companies and researchers, but I didn’t try to list those resources in an already-lengthy article.
Here are a couple of my old blogs for ESET that include the use of similar techniques.